Updated 3:19 pm Pacific Time: A method to ‘immunize’ yourself against this ransomware variant has been found. I have posted the details towards the end of the post along with the batch file you are running. This file is as simple as creating C: \ Windows \ perfect and marking it as read-only.
Update PST 2 on Tuesday at 7 pm: The initial transition has come from a company called Maycock that dissolved. Their systems were infected, and they then gave an update to spread the infection. Maycock is disputing the charge. Sources: Talos quoted on ZosNet, Forbes, and FireEye.
This is a public service announcement from Wordfence due to the widespread and severe nature of this attack. A major ransomware attack targeting Microsoft Windows systems is affecting companies and systems, many of them globally significant.
What We Know
At the time of this writing, a new ransomware version is spreading rapidly around the world. There is no consensus in the security research community, so the following information is provisional:
Ransomware has been dubbed “Petya.” It spreads using two different adventures. You do not need to click on anything or take any action. It can spread through the network in your system. This is why it is having such a broad impact and why you must update your order for your security.
For the technically minded: This ransomware is exploiting a vulnerability in Microsoft Office when handling RTF documents (CVE-2017-0199). It uses a vulnerability in SMBv1, which is the Microsoft file-sharing protocol. This second vulnerability is described in Microsoft Security Bulletin MS17-010.
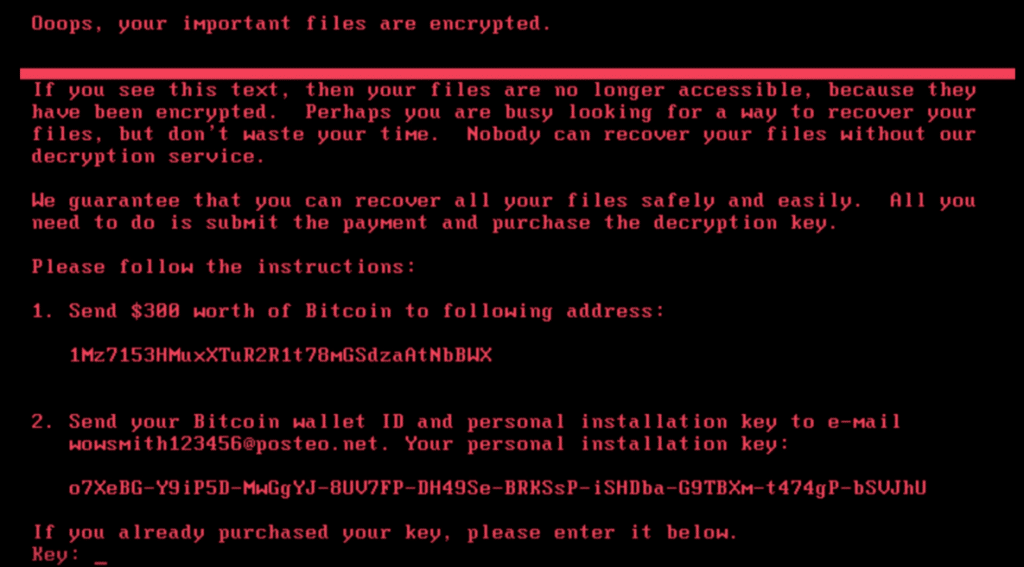
Ransomware has affected a large number of companies, organizations, and governmental organizations internationally. The following is a screenshot of the ransomware page you are facing after your files are encrypted:
Colin Hardy has provided a behavioral analysis of Petya, including a video demonstration of malware in action:
What To Do
If you have not already done so, you should immediately install the MS17-010 patch from Microsoft.
If you currently run an unreleased Windows system, you may not have time to patch it before it becomes infected. Consider shutting down your machine, if possible, and leave it off the network until there is a consensus in the research as to how it exploits and defends against it.
If you are technically competent, we recommend you block the network access to the 445 port on your Windows workstation. If you are a security professional, then you want to monitor the traffic at that port.
Keep an eye on the Microsoft Security Response Center, where they expect formal guidance to be released soon.
Update your anti-virus definitions and run scans on your system. You can find which anti-virus products are detecting the current version of Petya on this VirusTotal page. I linked to one of the files involved in the transition. The page shows that AV vendors are currently tracing this file. The green checkmark means that the data has not been received from that AV vendor (this defendant).
Who This Has Affected So Far
- A Ukrainian state power company and the main airport of Kyiv were among the first to report the issues.
- The Chernobyl nuclear power plant has to monitor radiation levels manually after forcing it to shut down Windows systems that use its methods.
- Antonov aircraft is reported to be affected.
- Copenhagen-based shipping company Maersk is facing outages in several IT systems and several business units.
- Food giants Modalz, who make Oreo and Toblerone, have also become a hit.
- Netherlands-based shipping company TNT was also a hit.
- French construction company St Gobain is affected.
- Pharmaceutical company Merck says they have systems affected.
- Law firm DLA Piper became a hit.
- Heritage Valley Health System, an American hospital operator, has also been hit.
- Kyiv’s metro system has stopped accepting payment cards because they were affected.
- The list is long and growing; Just a snapshot above.
The list is long and growing; the above just a snapshot.
Strong Incentive for Attackers
Many are reporting the notion that the South Korean hosting company paid a $ 1M ransom a week ago to recover their data, which has created a significant impetus for future ransomware attacks.
This has resulted in this new location of attacks affecting the system globally.
Coverage of This Story
- Symantec analysts have confirmed that Petya is similar to WannaCry.
- The BBC is providing excellent coverage.
- Caitlin Cimpanu is, as always, providing excellent coverage. He is reporting that Dakio, the author of Patty, where Patty’s author is hosting an inbox to handle ransom responses, has closed that inbox. This means that if you are hit, you cannot contact the ransomware writer to pay the ransom, and your data may be permanently lost.
- Ars Technica also has Dan Goodin Over covering the story.
- Real-time information is emerging on Twitter from security researchers.
- Thanks to TruStar for providing additional analysis.
Update 3:19pm PST: A Vaccine has been Found
Researchers have found a ‘vaccine’ against this new version of Petya against encrypting your files in the last few hours. They find that if a file exists, the encryption routine will not run.
Amit Semper found that other security researchers confirmed his findings.
To vaccinate a machine against this ransomware, create a perfect file in the C: \ Windows folder and mark it as read-only. The following batch file etiquette of BleepingComputer will work for you:
https://download.bleepingcomputer.com/bats/nopetyavac.bat
This post from BleepingComputer also includes instructions for manually creating the file if you would prefer to do so. Once this file is created, the encryption routine for this specific ransomware version will not run and encrypt it.
Help Keep the Community Safe
We recommend telling your friends and family about this fast-spreading campaign or urging them to help you stay safe.